程序的目的是在redhat和AIX上同时运行,对于很多指令,使用Redhat完成了,但是AIX上没有,这时,我们选择Alias的方式,在AIX的Env中,提供具备这样功能的指令模块。
下面是研究怎么实现redhat iptables的stub.
Step (1)about port <=> [inbound ,outbound]
查看端口占用情况:
Issue the command:(as 389 it the port you want to seek )
netstat -Aan | grep 389
this will return:
f1000089c27a2358 tcp4 0 0 *.389 *.* LIST EN
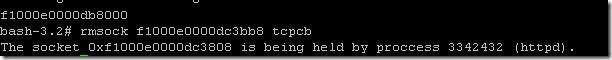
The next step is to take this value that was generated, f1000089c27a2358 and run it against the rmsock command:
rmsock f100089c27a2358 tcpcb
this command will return the process that is holding the socket.
The socket 0xc27a2000 is being held by process 204914 (ndsd).
Step (2)ipsec
什么是ipsec?
ipsec是IEFT提出的network管理标准工具。
ipsec的指令集:
Filters can be defined via the SMIT panel at the fastpath ips4_add_filter or via the command line, using the genfilt command. The SMIT method presents a screen similar to the table in the previous section. To create the filter "by hand", the following flags to the genfilt command are used to specify the attributes of the filter rule:
-v
The IP version to which this filter applies. Valid values are "4" and "6"-n
The filter ID, or number: The new rule will be added before the number specified with this flag. If not specified, the rule will be added to the end of the filter rules table.-a
The "action" of the rule: valid values are "P" (permit) and "D" (deny)-s
The source address: Specify either a fully qualified domain name (FQDN) or an IP address of the host or network to which this rule will apply. The value "0.0.0.0" specifies all IP addresses.-m
The source subnet mask: This will be used with the source address in determining whether this filter rule matches. The value "0.0.0.0" specifies all subnet masks.-d
The destination address: Specify either the FQDN or the IP address of the interface for which incoming packets should be matched against. The value "0.0.0.0" specifies all IP addresses on the system.-M
The destination subnet mask: This will be used with the destination address in determining whether this filter rule matches. The value "0.0.0.0" specifies all subnet masks.-g
Specifies whether this rule applies to source routed packets. Valid values are "Y" (yes) and "N" (no).-c
Protocol: Specify the protocols which will be matched by this filter rule. Valid values are "udp", "icmp", "tcp", "tcp/ack", and "all".-o
Source port/ICMP operation: This is the comparison operator that will be used in matching the source port of the packet to this rule. Valid values are "lt" (less than), "le" (less than or equal to), "gt" (greater than), "ge" (greater than or equal to), "eq" (equal), "neq" (not equal), or "any".-p
Source port/ICMP type: This value will be compared to the source port of the packet for possible matches.-O
Destination port/ICMP operation: This is the comparison operator that will be used in matching the destination port of the packet to this rule. Valid values are the same as for the "-o" flag.-P
Destination port/ICMP type: This value will be compared to the destination port of the packet for possible matches.-r
Routing/Scope: Specifies whether the rule will apply to forwarded packets (R), packets destined or originated from the local host (L), or both (B).-w
Direction: Specifies whether the rule will apply to incoming packets (I), outgoing packets (O), or both (B).-l
Logging: Specifies that an entry to syslog will be sent for packets that match this rule. Valid values are "Y" (yes) and "N" (no).-f
Fragmentation control: Specifies whether the rule will apply to fragment headers and unfragmented packets (H), fragment headers and fragments only (O), unfragmented packets only (N), or all packets (Y).-i
Interface: specifies the interface on which this filter rule applies. Valid values are the logical names of interfaces (en0, tr0, lo0, etc.) or "all" for all interfaces.
ipsec四个命令:
To work with TCP/IP filters you only need a few commands, which is explained here and then used in the next section. If you're familiar with AIX commands you see that these follow the same logic of having descriptive prefixes in their names, like mk, ls, and rm, followed by the filt suffix.
- lsfilt: List filters rules present in the table. When created, each rule is assigned a number, which can be easily seen using this command.
- genfilt: Adds a filter rule to the table. This is the one you use to create new filters. If you do not specify a position with the
–nparameter, the new rule is added at the end of the table.
- chfilt: Used to change existing filter rules. You need to provide the rule ID to indicate which rule you want to modify. Rule 1 is the default rule and can't be changed with this command.
- rmfilt: The
rm suffix should sound familiar with any UNIX administrator. You use this command whenever you have to remove a filter rule providing its rule ID.
- mkfilt: This is a key command that allows us to activate or deactivate the filter rules in the table, enable or disable logging for filters, and change the default rules. For the changes done to the filters table to take effect, you'll have to run this command with some arguments.
Refer:http://www.darklab.net/resources/aix-ipsec-filtering.html
http://unix.ittoolbox.com/groups/technical-functional/ibm-aix-l/implementing-ipsec-on-aix-machines-1332621
http://www.ibm.com/developerworks/aix/library/au-aixfiltering/index.html
使用过程:
(1)启动/关闭
# smitty ipsec4
(2)是否启动
# lsdev -l ipsec_v4
(3)做个改变
# chfilt -v 4 -n 3 -i en1
Filter rule 3 for IPv4 has been changed successfully.
#
(4)添加新的Rule
## Rules to reject traffic to the Web Application not coming from the Proxy
# genfilt -v 4 -a D -s 0 -m 0 -d 172.16.10.45 -M 255.255.255.255 -g N
-c tcp -O eq -P 80 -r L -w I -l Y -f Y -i all
(5)设置log
Now, you are going to configure the syslog daemon to log entries coming from the IP filters in a file that you specify.
## Backup syslog.conf file before modifying it.
# cp /etc/syslog.conf /etc/syslog.conf.bak
## Append entry for IP filters logs.
# echo "local4.debug /var/adm/ipsec.log" >> /etc/syslog.conf
## Create log file and set permissions (permissions may depend on
## company policies)
# touch /var/adm/ipsec.log
# chmod 644 /var/adm/ipsec.log
## Refresh the syslog subsystem to activate the new configuration.
# refresh -s syslogd
0513-095 The request for subsystem refresh was completed successfully.
(6)配置更新,上面的更新不会立即生效,除非运行下面的命令
# Start the log functionality of the filter rule module
# mkfilt -g start
# # Activates the filter rules
# mkfilt –u
Step (3) iptables
iptables 是linux中防火墙流行的管理工具
针对本文的作用,仅仅说明一种使用,若要详尽的了解,需耐心的阅读一个非常优秀的文章,链接如下:
Refer:http://man.chinaunix.net/network/iptables-tutorial-cn-1.1.19.html
or http://linux.ccidnet.com/pub/html/tech/iptables/index.htm
我们只是需要使用iptables像外界提供访问本机资源的端口:
httpPort=80
httpsPort=443
adminPort=8008
那么就使用下面的命令:
cmd 1 :iptables -A INPUT -p tcp --dport ${port} -j ACCEPT
cmd 2 :iptables -A INPUT -p tcp -s localhost -j ACCEPT
cmd 1 .在filter表上添加一条规则,如果socket pack来自TCP且push到${port}端口,就接收。
cmd 2 .在filter表上添加一条规则,如果源IP地址是本机,就接收。
Step (4)mock iptables
如果是用IPsec来实现打开端口,允许访问的话,是这样:
genfilt -v 4 -a P -s 0.0.0.0 -m 0.0.0.0 -d 127.0.0.1 -M 0.0.0.0 -g Y -c tcp –o any –p 0 -O eq -P 80 -r B -w B -l N -f Y -i all
mkfilt -u
所以,就是这样做一个mock
#
# cloud_iptables - simulate iptables
#
function aix_iptables
{
echo "aix_iptables:[$@]"
port=""
while [ $# -ne 0 ]; do
case $1 in
--dport)
port=$2
genfilt -v 4 -a P -s 0.0.0.0 -m 0.0.0.0 -d 127.0.0.1 -M 0.0.0.0 -g Y -c tcp –o any –p 0 -O eq -P $port -r B -w B -l N -f Y -i all
shift 1
;;
-s)
sourceip=$2
genfilt -v 4 -a P -s $sourceip -m 0.0.0.0 -d 127.0.0.1 -M 0.0.0.0 -g Y -c tcp –o any –p 0 -O any -P 0 -r B -w B -l N -f Y -i all
shift 1
;;
*)
shift 1
;;
esac
done
}
但是,这还没有结束
使用iptables时,我们是这样:
iptables -A INPUT -p tcp -s localhost -j ACCEPT
service iptables save
语句1 用来实现添加一条 rules
语句2 用来使变更生效
所以,还需要mock service 方法,这样,在两个平台中,语句1和语句2就都完成了打开一些防火墙端口的功能。
function aix_service
{
if [ "$1" = "iptables" ]; then
mkfilt -u
else
echo "aix_service $*"
fi
}
对于系统的判断:
function on_AIX
{
test "`uname`" = "AIX"
}
如果是AIX系统的话,就要在AIX上执行aliases了。
if aliases_on_aix ; then
shopt -s expand_aliases # enable expand aliases,keep it on
alias sudo='aix_sudo'
alias hostname='aix_hostname'
alias iptables='aix_iptables'
alias chkconfig='aix_chkconfig'
alias service='aix_service'
alias
fi
上面是在AIX的bash环境下进行的。